For the 11th year in a row, the healthcare industry had the highest average data breach cost. Healthcare data breach costs increased from an average of $7.13 million in 2020 to $9.23 million in 2021. For reference, the average cost of a data breach across all industries in 2021 was $4.24 million. Now more than ever, it’s crucial that your healthcare organization prioritizes data protection.
Although some healthcare providers worry that an enterprise resource planning (ERP) system will be a prime target, it’s much easier to use adequate resources and technology to protect information stored in one place. That being said, not all ERPs offer the same calibre of data protection. This blog delves into the challenges facing healthcare ERP security, so you can adopt the best practices for protecting your data.
Click on the healthcare security topic you’re most interested in to skip ahead:
- Cyber-attacks vs security breaches
- Why decentralized ERPs might leave your data vulnerable
- The cost and cause of healthcare security breaches
- The aftermath of a security breach
- Protect your healthcare data with these best practices
Cyber-attacks vs security breaches
Before getting to the nitty-gritty of cybersecurity, it is essential to distinguish between cyber-attacks and security breaches (as many get the two confused). A cybersecurity attack is a severe offence whereby data or confidential information is stolen by electronic means, including ransomware and hacking. A security breach, also known as a data breach, is any unauthorized or unintentional disclosure of confidential information.
Therefore, all cyber-attacks are security breaches, but not all security breaches are cyber-attacks. This blog focuses on security breaches of all kinds, as they cause concern and complications for security experts and impact patients, stakeholders, employees, organizations and businesses. To best defend the data in your healthcare ERP, it’s essential to understand the common causes and symptoms of a security breach.
Why decentralized ERPs might leave your data vulnerable
If security is a vital concern for your organization, you must research the pros and cons of centralized and decentralized ERP systems before you invest. Centralized systems consolidate information across various entities and departments, such as accounting, warehouse, inventory, HR, etc. Unifying data across different business units allows them to function efficiently and generates a seamless data flow stored within a centralized database.
Decentralized systems silo data by entity offering management maximum flexibility; however, their defence protocols are usually stretched too thin, creating a spider web of cracks in your security. Every time your data moves between different systems, there’s a risk of a security breach. Each data transfer needs its own form of high-level security, and each of these processes needs to be monitored and routinely updated to ensure that nothing slips through the cracks.
The protocols needed to achieve the same level of security in a centralized system are easier to keep track of than in a decentralized system. You can also usually afford better protection when using a centralized system because your budget isn’t split across multiple business units and processes.
A successful cyber-attack can be very lucrative for hackers but incredibly detrimental to your organization. In the eyes of cyber-criminals, critical data like patient and employee personal identifiable information (PII), patient personal health information (PHI), financial information, and proprietary formulas are the crown jewels of your organization. Therefore, protecting your data with every available precaution is necessary.
Read more: How healthcare providers benefit from implementing an ERP
The cost and cause of healthcare security breaches
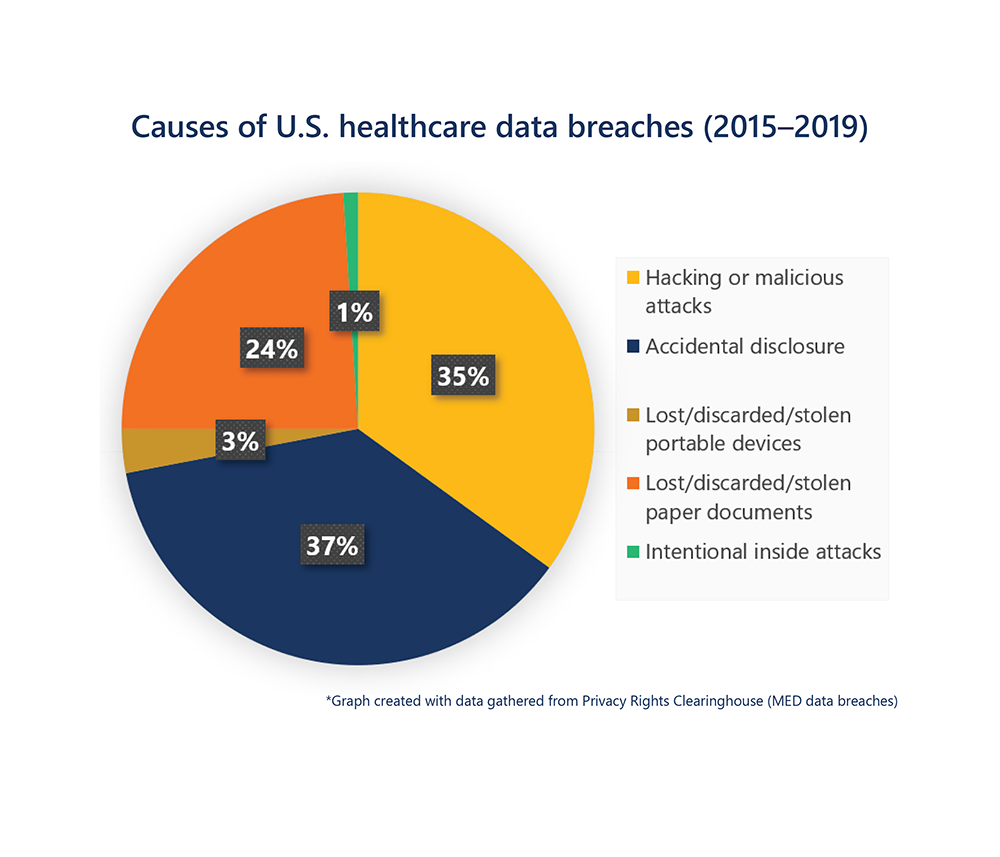
The three prominent causes of security breaches in healthcare arise from accidental disclosures, lost/stolen/discarded physical records or devices, and hacking or malicious attacks. It would be best if you had security measures to prevent all three types of breaches from occurring.
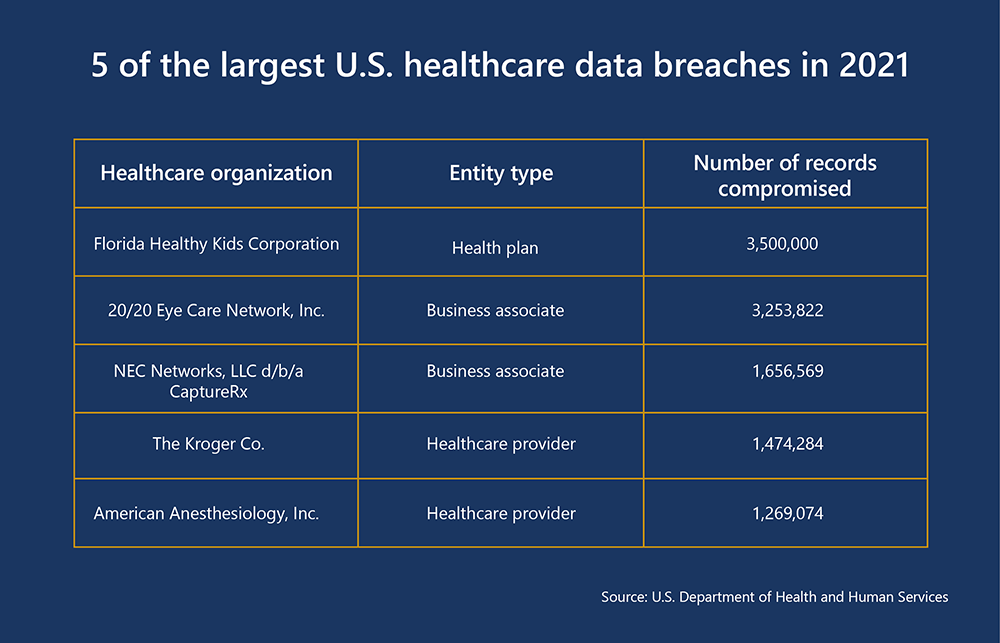
In the first half of 2021, the U.S. Department of Health and Human Services reported that 72% of healthcare security breaches were due to hacking incidents. One of the biggest data breaches of 2021 uncovered a seven-year security breach targeting the Florida Healthy Kids Corporation compromised upwards of 3.5 million records. However, the 2015 Anthem security breach remains the worst case for the industry, with over 80 million documents leaked from a cyber-attack. Anthem settled multiple class-action lawsuits for $115 million and paid the fine of $16 million to resolve HIPAA violations uncovered during its breach investigation.
Despite the recent increase in hacking and malicious attacks, it’s not the only way to compromise healthcare ERP data. The other two leading causes are serious threats. Health Share of Oregon compromised 654,362 records due to a laptop stolen from their patient transportation vendor in November 2019. Elkhart Emergency Physicians leaked 550,000 records from 2002–2010 because a third-party vendor didn’t shred patient files before disposing them.
Accidental disclosures commonly occur from sending emails containing PHI to the wrong recipient or leaving servers publicly accessible. In 2018, an employee at Independence Blue Cross accidentally uploaded the names, birthdays, diagnosis codes and provider information of 17,000 members to the company website.
The aftermath of a security breach
In 2021, the average cost per record lost in a security breach was $161, and if PII was compromised, that price increased to $180. However, the cost of a cyber-attack is often more than just the money spent to restore and re-secure your healthcare ERP systems—recovering from a security breach impacts the day-to-day functionality of your business. The downtime while the systems are out of operation will result in a loss of revenue and productivity. Anyone’s job could be at risk, and if production drops to a low enough point, you may be facing the possibility of letting people go and paying them damages.
Most importantly, your patients care about the safety of their PII, so a breach could cause them to lose confidence in your organization—jeopardizing your brand value and compromising your company’s reputation. These risks and improper handling of a cyber-attack could have a negative influence on future sales. In some ways, the loss of trust imposed by a security breach is a more significant threat to your revenue than the costs of recovering the data. Without essential safeguards in place, ERP systems are vulnerable to attacks, which is why it’s so important to invest in solutions with robust cybersecurity measures to protect your organization.
Protect your healthcare data with these best practices
Advancements in hacking and cyber-crime require a shift in mindset. It is no longer enough to focus on keeping the bad guys out; the bad guys are in your network. Now, it’s essential to consider how to protect your data from getting stolen. In 2021, it took companies an average of over 200 days to identify and 75 days to contain a data breach; however, if they kept the lifecycle of a data breach below 200 days, they reduced the average cost by $1.26 million. If there’s a security breach, can you spot it, contain it, and deal with it as soon as possible? To answer this question, let’s go through some of the best cybersecurity practices.
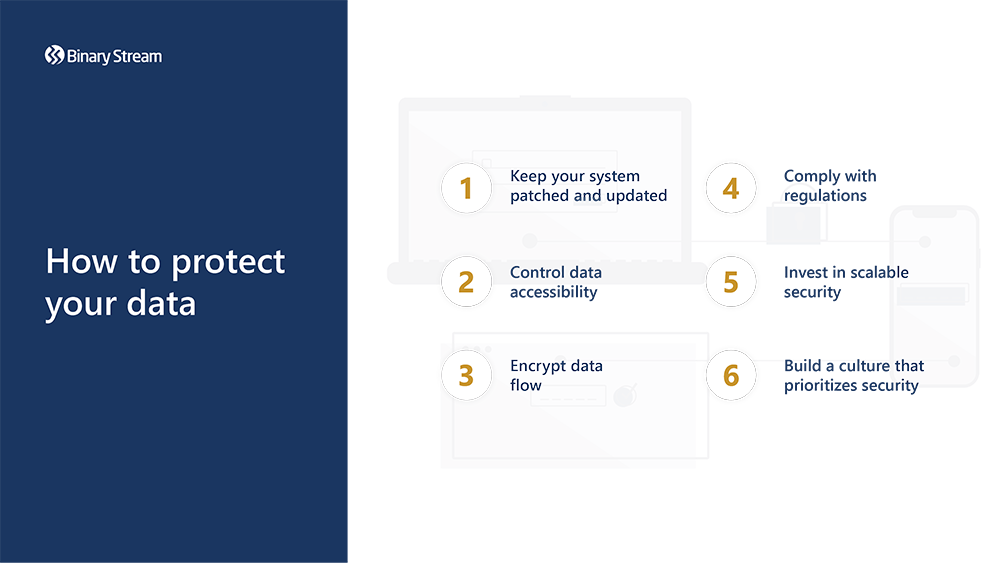
Keep your system patched and updated
The very first thing you should do is update your system and, going forward, ensure to keep it updated. Cyber-criminals actively look to exploit outdated healthcare ERP software because it’s more vulnerable without the latest security patches, and it’s harder to rectify technical issues, like crashes, when you’re running an unsupported version of the software. To ensure that you’re always running a fully up-to-date system, it can be a good idea to approve automatic updates or set up a schedule that will install available updates during non-operating hours. Even better, invest in software with a reputation for consistent updates and robust security features. For example, Microsoft has a very secure ecosystem and invests $1 billion in cloud security each year.
It’s not just the ERP system that needs to be routinely updated. Users are accessing the system in multiple ways. Any device that accesses the system must be secured and updated. If any of the methods are compromised, it poses a risk to the entire ERP application.
Control data accessibility
Successfully managing staff across different departments and locations can be a challenge, so you must consider what access rights each individual needs to do their job effectively. For example, the CFO needs access to performance reports across all entities to understand the big picture for the organization. Still, employees from one entity don’t necessarily need access to reports from the other entities. Similarly, you may want junior accountants to enter data but not edit existing data without requesting additional permissions. Full access rights and permissions should not be the default, and each user should have strictly controlled data accessibility.
The IT department should also monitor and assess the risk of every device that connects to the network, creating an inventory of approved devices. It is crucial to reassess the level of access rights awarded to an individual as changes occur within the organizational structure of your employees. Opportunities for re-evaluation include hiring new employees, changing job roles, after promotions, or after mergers and acquisitions (M&A).
Encrypt data flow
The nature of ERP systems means a constant stream of data between different departments and across a multitude of devices. In addition to protecting your network through security tactics like a virtual private network (VPN) or a firewall for local connections, your organization must invest in solutions with advanced encryption. Using these methods in tandem will offer you the absolute best defence for your data flow, even across wireless networks and messaging systems. Data encryption has the added benefit that it will help keep your organization HIPAA compliant by protecting personal information from a security breach.
Comply with regulations
Ensure that your security is up to the standards of the rules and regulations governing your geographic region. The healthcare industry is highly regulated, and compliance is non-negotiable, especially regarding data security. For example, the minimum fine for willful violations of HIPAA Rules is $50,000. The maximum criminal penalty for a HIPAA violation by an individual is $250,000, with the likely addition of restitution paid to the victims and jail time.
Examples of national security compliance standards that apply to healthcare:
- United States: HIPAA Security Rule
- Canada: PIPEDA and The Privacy Act
- European Union: General Data Protection Regulation (GDPR)
- Japan: Act on the Protection of Personal Information (APPI)
- Brazil: General Data Protection Law (LGDP)
Read more: A guide to creating a culture of healthcare compliance in your organization
Invest in scalable security
Whether your organization has a handful of clinics or a network of hospitals, your security software must maintain a high level of data protection throughout your growth journey. Relying on older technology coupled with constantly adding new devices will put a strain on your security measures. When choosing an ERP system, it is best to look for ones that offer scalable security options, ensuring that your data remains safe through growth. Some even come with industry-specific features or add-ons that can help you to stay compliant.
As much as upgrading your systems to newer technology can be time-consuming and costly, sometimes it is the best decision to make. Systems that are out of date not only slow down the efficiency and productivity of your organization but can also pose a severe security risk to your data. Knowing when it is appropriate to upgrade your technology is vital. If you notice that future ERP software updates would be unsupported by your current system, that’s a good indication that it’s time to think about upgrading. Keeping up with advancements will help you determine whether there is value in updating your technology.
Build a culture that prioritizes security
Social engineering is one of the most frequently used methods by cyber-criminals to manipulate humans. Spear phishing emails prey on your employees’ emotions and can look legitimate enough to dupe them into leaking vital healthcare ERP data. Undertrained staff who regularly handle sensitive data may be a greater risk to your business than external cyber-attacks.
Developing a security training program that features regular and easily understood sessions will enable your employees to maintain healthy security habits. Implementing two-factor authentication, routinely changing passwords, and not exporting data across multiple systems (like storing ERP data in spreadsheets and sharing it via email) are just a few protocols that can greatly increase your security if practiced consistently.
In addition to frequent security training, an incident response (IR) team and IR plan testing are invaluable tools in the event of a security breach. In 2021, companies with an IR team and IR plan testing saved on average $2.46 million off the total cost of a data breach. The IR plan contains some variation of six steps; preparation, identification, containment, eradication, recovery, and lessons learned. By creating a procedure for handling security threats, you can minimize the damage while maintaining a record of the incidents to prevent follow on attacks or similar events in the future.

